Contents
- Introduction
- Scope
- Definitions
- The Risk Management Process
- Risk identification
- Risk assessment and assessment criteria
- Risk Appetite
- Risk tolerance
- Risk interactions
- Risk prioritisation
- Assigning a risk score
- Opportune Risks
- Risk response
- Reducing risk - types and styles
- Reviewing and monitoring risks
Appendices
Introduction
This guidance covers the ways in which we manage strategic, project and operational risks and should be read in conjunction with the NHSCFA Risk Management Policy and Risk Appetite Statement.
It should be read by the Board, the Executive Management Team (EMT) Senior Management Team (SMT), Leadership Team (LT) and staff who are delegated to own, manage or action specific risks or issues.
The guidance is available for everyone to read on the internal staff intranet (Go2) and the LT should encourage all their staff to become familiar with it.
The risk management policy makes it clear that all staff are responsible for identifying potential risks and alerting their managers accordingly. Risk management is a standing item on all business teams meeting agendas.
Scope
This guidance seeks to help those involved in taking action or ownership of risk by:
Describing the risk management process from end-to-end, taking into account the specific methods and documentation used within the organisation to deal with risk.
Describing what constitutes a risk and to identify an event or course of action as a potential risk or opportunity.
Taking effective action to assess the risk and to report their findings to managers and the board.
Contributing to their team and division’s risk profile in accordance with organisational protocols.
Participating effectively in discussions about how risks may be managed and to take action accordingly.
Monitoring and reviewing the success or otherwise of a risk management strategy in respect of individual risks.
Contributing to our understanding of risk and the lessons we can learn from risk management actions whether positive or negative.
Definitions
The organisational Risk Management Policy defines risk as:
“the effect of uncertainty on objectives: whether positive opportunity or negative threat. This means that risks may involve both positive and negative outcomes”.
Risk is sometimes conflated with the term “issue”. An issue is defined as an event that has happened or is happening. It is a ‘known’ as opposed to an ‘unknown’ quantity. The outcome of the actions and events is no longer subject to uncertainty. The consequences may be observed and measured. However, that is not to say that new risks will not emerge as the issue continues to exist.
At this point it is necessary to explain the difference between an inherent risk and a residual risk.
An ‘inherent’ risk is one that is unmitigated or changed by any risk management action we might decide to take. A ‘residual’ risk is the risk that remains once the inherent risk has been subjected to risk mitigation or management. The figure below is an illustration of the difference between the two.
Fig 1
| Event | Inherent risk |
|---|---|
| Getting into the driving seat of a car, turning on the engine and moving off. | Damage to vehicles and injury to driver, other road users and pedestrians |
| Risk management action | Residual risk |
| Instructions to check mirrors and use indicators appropriately before moving off and to wear a seat belt | Reduced possibility of damage to vehicles and injury to driver, other road users and pedestrians |
| Further risk management action | Residual risk |
| Driver must obtain permission to move off from passenger who will ensure that mirrors are checked, indicator used appropriately and seat belt is properly worn | Further reduction of the possibility of damage to vehicles and injury to drivers, other road users and pedestrians |
| Further risk management action | Residual risk |
| In addition to the two measures above the car is immobilised, that is mechanically unable to move, until such time as the passenger is satisfied that all safety precautions have been undertaken. The passenger will then flick a switch which will disengage the immobiliser | Even less possibility of damage to vehicles and injury to drivers, other road users and pedestrians |
There are a number of terms used in the theory and practice of risk management which might be unfamiliar. A full glossary of relevant terms is set out at Appendix A.
The Risk Management Process
Figure 2 below sets out in broad terms the stages our organisation will go through from the very start of the risk management process to its conclusion.
Fig 2
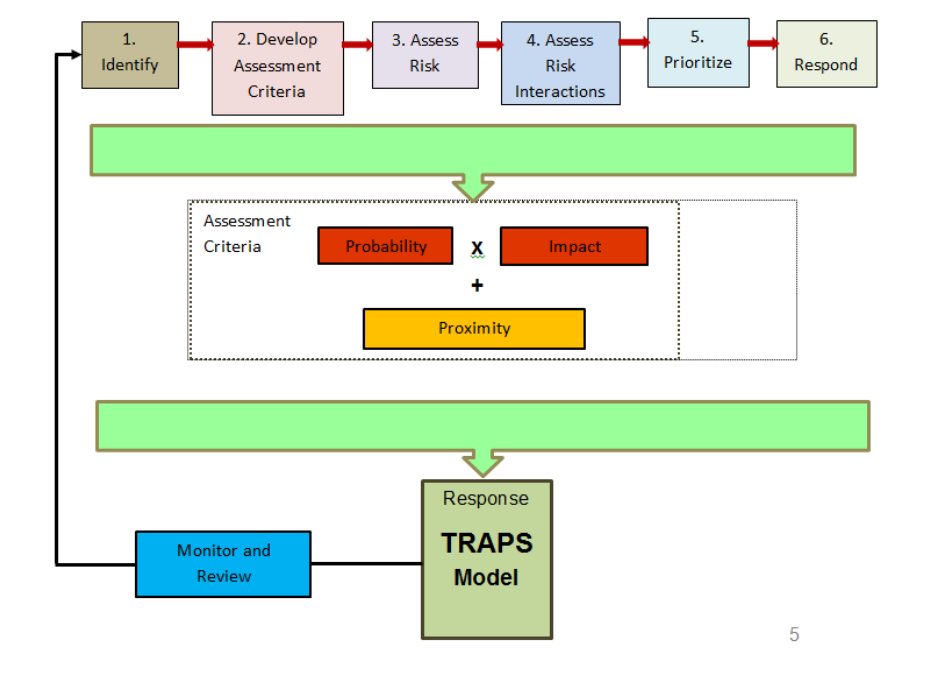
However it is not quite as cut and dried as it might first appear. Our organisation may tolerate controlled risks for long periods of time and consequently we need to frequently review and monitor risk over an extended period. This may identify further associated risks and we might have to repeat the whole cycle or parts of it. The following paragraphs will lead you through each stage.
Risk identification
All employees have an obligation to identify and flag events or courses of action which may bring about our exposure to risk. Some risks are so insignificant or so easily managed that they need not feature in our risk management register or even in local risk profiles.
We are primarily concerned with risks which may have an effect on the achievement of one or more of our operational, project or strategic objectives.
Identified risks are been placed into one of six broad overarching risk categories.
Fig 3| Risk Aspect | |
|---|---|
| Service Disruption | Risks that may jeopardise the organisation’s continuing existence, operation of its functions or could lead to a loss of stakeholder confidence. |
| Legal, Regulatory, Compliance & Finance | Risks that may cause any material breach of statute, regulation, professional standards or would adversely affect the organisation’s overall financial strength and long-term viability. |
| Safety Health & Environment | Risks that would adversely affect the health and wellbeing of staff and visitors in the workplace resulting in a breach of regulatory and legislative standards. |
| Reputation & Credibility | Risks that could expose the organisation to additional scrutiny e.g. in respect of decisions on policy, information security, employee conduct or organisational culture. |
| Personal Information/Bulk Data | Risks that could adversely affect the organisation’s reputation, credibility, compliance or stakeholder confidence in the processing of personal data. |
| Technology & Cyber-Security Threats | Risks/threats that could expose the organisation to harm or loss resulting from breaches of or attacks on its information systems or technical infrastructure. |
Once identified and acknowledged as a potential risk the next stage is to decide on which criteria to use when we assess the gravity of a risk. The system we use for this purpose is used throughout the NHS and other organisations in both the public and private sectors.
Risk assessment and assessment criteria
The weight of each potential risk is assessed using three criteria:
- Probability
- Impact
- Proximity
Very simply, probability is a judgement as to the likelihood of a risk actually being realised.
Take as an example the risk that a substantial object from space will collide with the Earth within the next 100 years. It is possible but highly unlikely. If we were to extend the time period, however, we can state with a degree of confidence from studies of past impact events that such an event will become more likely. The probability of the risk being realised increases.
We then score the level of probability on a scale of 1 to 5. See figure 4 below.
Fig 4 Probability Matrix
| Probability | 1 | 2 | 3 | 4 | 5 |
| Descriptor | Rare | Unlikely | Moderate | Likely | Almost certain |
| Frequency: How often might it / does it happen? | This will probably never happen or recur. Not expected to occur for years | Not expected to happen or recur, but it is possible. Expected to occur at least annually | Might happen or recur occasionally. Expected to occur every quarter | Will probably happen or recur, but it is not a persistent issue or circumstance. Expected to occur at least monthly | Will undoubtedly happen or recur, possibly frequently. Expected to occur at least weekly |
Our errant space object would probably rate as a score of 1 over a shorter time period. However, if the time limit was to be extended indefinitely then such an event becomes a near certainty.
The next factor we need to take into consideration when assessing risk is the impact or consequences should the risk be realised. In the event of the same Earth impact scenario the consequences are likely to be catastrophic!
We again assign a score from 1 to 5 regarding the impact. See figure 5 below.
Fig 5
| Impact Level | Minor 1 | Insignificant 2 | Moderate 3 | Major 4 | Catastrophic 5 |
We then combine the scores allocated to probability and impact by multiplying one by the other. This gives us a selection of potential risk scores between 1 and 25. This is shown in figure 6. These scores will be calculated by the IT application.
Fig 6
| Impact | ||||||
| Probability | ||||||
| 1 | 2 | 3 | 4 | 5 | ||
| 5 | 5 | 10 | 15 | 20 | 25 | |
| 4 | 4 | 8 | 12 | 16 | 20 | |
| 3 | 3 | 6 | 9 | 12 | 15 | |
| 2 | 2 | 4 | 6 | 8 | 10 | |
| 1 | 1 | 2 | 3 | 4 | 5 | |
The final factor we need to take into account is proximity. How soon do we think our exposure to the risk will occur? If we believe a risk will be realised sooner rather than later then we will need to take this into account. We don’t assign a numeric value to this, but we do use a Red-Amber-Green (RAG) rating. See figure 7 below.
Fig 7
| Proximity and timescale for dealing with the risk | Within one year | Within six months | Within three months | Within one month | Within one week |
| Descriptor | |||||
| Lifecycle / Process | At some stage in the future | Prior to the end of the lifecycle or process | Prior to the end of the next stage or phase | Prior to the end of the next stage or phase | Prior to all other activity being carried out |
It is conceivable that urgency to respond may tip the balance in deciding which order to tackle two or more risks which have identical probability x impact scoring.
Risk Appetite
The risk appetite sets out the level of risk that the NHSCFA is willing to accept. Managers and Team Leads in the organisation are expected to use this to guide their decision making. This is set out in the NHSCFA Risk Appetite Statement.
The risk appetite of the NHSCFA represents the organisation’s decision on the appropriate exposure to risk that it will accept in order to deliver its strategic objectives.
Lines of Defence
It is the responsibility of the Board, the Audit, Risk & Assurance Committee (ARAC) and the SMT to ensure that lines of defence are appropriately reflected in the organisation’s risk management processes. Together they have collective responsibility and accountability for setting the organisation’s objectives, defining the strategies to achieve those objectives and the establishment of governance structures and processes to best manage the risks in accomplishing them.
The ‘three lines of defence’ model (see Fig 8) distinguishes the three functions involved in effective risk management:
- functions that govern management control and reporting
- functions of oversight and governance
- functions that provide independent review, assurance and regulatory oversight
FIRST LINE - SMT and LT will be responsible for maintaining effective internal controls to ensure the achievement of KPIs, quality control and the ongoing review of objectives on a day-to-day basis.
SECOND LINE - Functional oversight may be provided by a variety of sources such as the Board, the DHSC Sponsor, SMT or Finance & Corporate Governance Unit. They will monitor the effectiveness of the risk management and mitigating practices employed to address the identified risks throughout the organisation.
THIRD LINE - This is provided by a number of independent review sources such as the National Audit Office, the Government Internal Audit Agency, or DHSC. This independent review provides assurance on the effectiveness of the organisation’s governance, risk management and internal controls, including the manner in which the ‘First’ and ‘Second’ lines of defence achieve risk management and control objectives.
Fig 8
| First Line of Defence: Management control and reporting | Second Line of defence: Functional Oversight / Governance | Third Line of Defence: Independent Review /Assurance /Regulatory oversight | ||
|---|---|---|---|---|
| Management Review | CFA Board (initial review) | CFA Board | ||
| KPIs | DHSC Sponsor(initial review) | Audit & risk Committee | ||
| Quality Checking | SMT | REMCO | ||
| Training | LT | Department of Health | ||
| Ongoing Review and Objectives | FCG | DH Sponsor | ||
| System Controls | Performance & Assurance panels | NAO | ||
| Segregation and Access Controls | Internal Governance & Assurance | GIAA | ||
| Policies / Procedures | IT strategy group | Cabinet office | ||
| Workforce Planning | Security forum | Third party assurance | ||
| Operational Risk Management | Assurance framework & BAF report | Accreditations | ||
| Exception Reporting | Counter Fraud & security management workplans | |||
| Other | Other | Other | ||
Risk tolerance
NHSCFA uses a standard 5x5 risk scoring matrix (see above) for assessing the impact and likelihood of identified risks. The SMT, Board and the ARAC have responsibility for monitoring and reviewing all risks scored outside of the organisation’s tolerance threshold and taking appropriate action.
Any risks rated at or above the minimum score are reported to the Business Unit Leads on a monthly basis. A risk score of (9+) is treated as a trigger for a discussion at the LT meeting, together with the Corporate Board Secretary and the Risk Management Lead, to determine whether the risk score is justified. Any operational risks considered to be correctly rated and identified as scoring 12+ will be escalated to the Risk Register Review Group (RRRG) to consider whether it should be classified as a corporate risk. The RRRG also reviews strategic and corporate risks, discussing recommendations to SMT for action.
Risk interactions
Before going on to explain how we respond to risk it is worthwhile noting one further question which we must consider. That is:
Do we face risks which are interlinked or capable of interacting with one another thus generating an aggregate exposure?
Risk prioritisation
How we decide to prioritise the order in which we deal with each risk is largely down to the scoring we have accorded to it, together with the urgency of the action required.
Through the organisational risk register, decision makers should possess sufficient information in sufficient detail to enable them to work out which risks need to be addressed and the priority for doing so.
Prioritising risk is very much allied to our intended response to each risk or opportunity. Resources are finite and this will also have an immense bearing on how we prioritise our responses.
Assigning a risk score
As part of the risk assessment process, each identified risk should undergo a three-stage evaluation:
- ‘Inherent’ - firstly, review as though there were no controls in place or the proposed controls in place are failing; then
- Residual - assume adequate controls are in place and are operating effectively; and now
- ‘Set a Score’ - this is achieved by implementing action to bring the risk in line (where possible) with the articulated appetite and tolerance level.
Opportune Risks
When positive risks occur they can often be managed as an opportunity and therefore it is equally important to prioritise actions and to concentrate on those opportunities that are most likely to bring about a successful outcome.
When deciding whether to take an opportunity risk the same principles apply. The costs involved in exploiting the opportunity must be justifiable in terms of the anticipated benefits and the controls should not lead to significant risks.
Risk appetite levels will depend on the circumstance and therefore, the risk responses for opportunity risks are categorised in a similar way to those for negative risks:
| E | EXPLOIT |
Ensuring the opportunity is realised.
| E | ESCALATE |
Where an opportunity arises that a business unit is unable to realise as they lack the requisite authority to take the necessary step.
| E | ENHANCE |
Increase the chance of the risk happening so that the benefits of the opportunity can be realised.
| A | ACCEPT |
No action is taken to realise the opportunity; it is left as it is and if it happens on its own, then the organisation will benefit from it (mainly used when the cost of the response is high and there is less chance of it occurring or the benefit does not outweigh the effort involved).
| S | SHARE |
Where a business unit is not capable of realising the opportunity on its own and so works together with another business unit or external stakeholder to realise the opportunity.
Risk response
Various risk response models exist throughout the private and public sectors. They are all quite similar in that they seek to ensure that all available options open to an organisation are considered before choosing the optimum response.
We currently use a standard model to categorise our response to risks. It is called the TRAPS model.
Fig 9
| T | TERMINATE |
| R | REDUCE |
| A | ACCEPT |
| P | PASS |
| S | SHARE |
We will look at each of these in turn.
| T | TERMINATE |
This means terminating the activity giving rise to the risk. This response might manifest itself by:
- abandoning a core business function
- deciding not to risk taking up an opportunity
- ceasing to carry out a course of action decided upon before the risk had become apparent
- ceasing an activity or function when it is clear that risk management actions have been unsuccessful.
Such a course of action may be the only viable option if reducing the inherent risk is impossible or would be too resource intensive to reduce successfully.
| R | REDUCE |
This is by far the most common response. The inherent risk having been identified and assessed is examined and methods of reducing the inherent risk and leaving an acceptable residual risk (having applied risk mitigation), will be agreed and implemented.
We will revisit reducing risk later on in this guidance as there are diverse methods of risk reduction which need further exploration. See paragraph 14 below.
| A | ACCEPT |
Some risks are unavoidable and are absolutely incapable of mitigation, (“they come with the territory”), or can only be reduced by a disproportionate expenditure of resources.
These are carefully monitored and reviewed.
| P | PASS |
This would involve transferring the risk elsewhere: For example, by outsourcing a function with inherent risks to another entity. An example of this can be found at Appendix B.
| S | SHARE |
This may involve forming a partnership with another organisation(s), with an agreement to share the exposure to risk. This arrangement is more difficult to arrange in that many public sector organisations have clearly delineated functions set out in primary or secondary legislation.
As mentioned previously there are several variations on this model in use in both the public and private sectors and they are all quite similar. It is worth looking again at risk reduction and the identification of different types of reduction styles/types, set out in HM Treasury’s Orange Book referenced earlier in the guidance.
Reducing risk - types and styles
Preventive controls
- These controls are designed to limit the possibility of an undesirable outcome being realised. The majority of controls implemented in organisations for the purpose of reducing risk tend to belong in this category.
- A familiar preventative control in the world of counter fraud is the separation of duties, see figure 10 below:
Fig 10
| Who | Function | Inherent Risks |
| Employee A Procurement Officer | Responsible for ordering goods and also authorising payment for them |
1. Employee A Orders goods or siphons them off for personal use. 2. Employee A colludes with suppliers to over-order, inflate prices or arrange for the supply of and payment for “phantom goods” |
| Preventative Control 1: Separation of duties. | ||
| Who | Function | Residual Risk |
| Employee B Finance Officer | 1. Responsible for authorising payment for goods ordered by Employee A. | 1. Collusion between Employee A and B 2. Collusion between Employee A and B and a third party |
| Preventative Control 2: Frequent unannounced management audit and stock checking | ||
Preventative Control 1 makes it much harder for either employee to act on their own to commit fraud. In order to ensure both sides of a fraudulent transaction match they will need to collude. The measure has reduced the probability of the risk being realised.
Preventative Control 2 reduces the likelihood of the realisation of the residual risk further. The imposition of management checks might deter either employee from defrauding the system. This measure might also reduce the loss to fraud through early detection, thus reducing the impact of the risk.
Another measure which would reduce the impact of the risk as well as its probability is introduced by Preventative control 3. See figure 11 below.
Fig 11
| Who | Function | Inherent Risks |
| Employee A Procurement Officer | Responsible for ordering goods and also authorising payment for them | 1. Ordering goods or siphoning off goods for personal use. 2. Collusion with supplier to over-order, inflate prices or arrange for the supply and payment for “phantom goods” |
| Preventative Control 1: Separation of duties. | ||
| Who | Function | Residual Risk |
| Employee B Finance Officer |
1. Responsible for authorising payment for goods ordered by Employee A. 2. Regular stock checks and audits of goods in and payments out. |
1. Collusion between Employee A and B 2. Collusion between Employee A and B and a third party |
| Preventative Control 2: Frequent unannounced management audit and stock checking | ||
| Preventative Control 3: All orders and payments over a certain value must be independently approved by a manager | ||
| Residual Risk: Collusion between Employee A, Employee B and manager(s) / auditors. Loss is likely to be limited | ||
Detective Controls
Preventative Controls 2 and 3 in figure 11 above also fall into the category of Detective Controls. Frequent unannounced audits and stock checks would minimise the impact of the risk by revealing the fact that the risk had in fact been realised. In essence this is damage limitation through early detection.Directive Controls
These are often found in Health and Safety risk management measures, such as compelling people to wear Hi-Viz clothing or hard hats in certain high danger areas.
In the security arena we might prohibit unauthorised persons from certain areas of the workplace, and more generally only allow staff with proven knowledge and skills to perform certain tasks.
In the case of our warehouse example in figure 10 above we could contractually oblige employees to submit to proportional searches of the person and/or vehicles as they leave the workplace.
Corrective Controls
Corrective Controls, as the name suggests, kick in after a risk has been realised. These might include insurance against theft in our example above. On an organisational scale they may be part of a business continuity plan in the event of major incidents beyond the control of the organisation.
Resourcing
All responses to risk must be proportionate and reasonable. Resources are finite and this is why it is important to accurately assess risk levels and monitor the success or otherwise of risk mitigation measures. This is equally important in cases where probability and impact actually decrease over time as it may be possible to reduce or even cease continuing risk management measures (close the risk) and reallocate resources.
Reviewing and monitoring risks
Once risks have been identified, assessed and managed it is essential that SMT and business units continue to review and monitor them. Each risk has an SMT owner who has overall accountability for the risk. See also paragraph 8.2.
A fundamental part of the regular review process will be to ensure that a full chronology of the actions taken are and recorded within the Management Reporting Tool (MRT) at each review period. Equally as important, the reviewer will also need to consider what if any impact, recent actions taken will impact on the risk’s current scoring.
The chronology of events will be crucial in assisting those internally and externally charged with auditing the management of the organisation’s risk register. An appropriately detailed chronology is vitally important to aid the understanding of the actions taken and the cause and effect of those decisions.
Business units may be challenged regarding the scoring of a risk and the reasons for escalation, by the Board Secretary and the Information and Risk Management Lead or as part of the Governance and Assurance function.
Unit Leads may be called upon to provide an objective and independent account of the adequacy of risk management processes and the management of individual risks.
This guidance and the overall conduct of risk management processes across the organisation shall be reviewed at least biennially.
Leadership Team members may be called upon to provide evidence of the assurance processes they have implemented, or have had implemented on their behalf, across their whole risk spectrum. This evidence should:
- be sufficient in scope and weight in that it includes key risks and gives assurance that the risks have been dealt with in accordance with the Risk Management Policy and this guidance
- refer to any risk management training undertaken
- be relevant
- be reliable
- be understandable
- be accurate and unbiased
- demonstrate that another person having undertaken a similar exercise would reasonably come to the same conclusion
Similar assurances may be requested at more frequent intervals by SMT, the Board or ARAC.
These assurances are demonstrated by way of the Board Assurance Framework (BAF), risk and issues report which is presented for review at the SMT and ARAC meetings.
The BAF risks and issues report captures details of open risks with an inherent score of 12 and above. The report forms part of the governance arrangements ensuring that the NHSCFA is held accountable to the Government and Department of Health and Social Care (DHSC).
The Risk Owners are responsible for ensuring that the risks are updated in MRT by the ‘risk actionee’ with sufficiently accurate detail to inform the ARAC and the Board of the current position.